install.sh installs everything you need to successfully execute Sovereign Stack on your management machine. You should go take a look at it, as it requires sudo.
Bare Metal Management Machine Requirements
The management machine itself should be Ubuntu Desktop 22.04 or later. It is recommended to use ZFS-based full disk encryption option along with a complex password. The bare metal machine must support the creation of VMs using incus to host the SSME.
About the Sovereign Stack Management Environment
install.sh creates the Sovereign Stack Management Environment (SSME). The SSME is a full VM that contains all the tools necessary for you to successfully control remote SSH and incus cluster endpoints. This SSME gets created when you run the install.sh script on your bare-metal management machine.
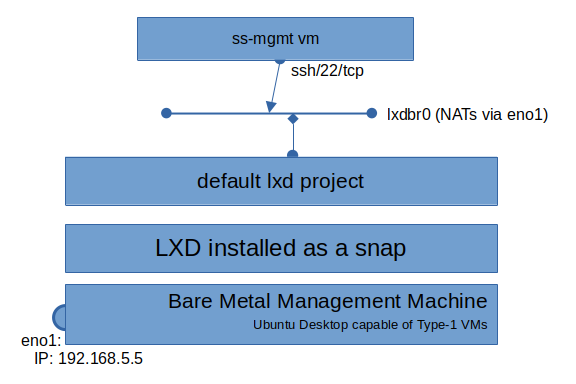
Sovereign Stack installs the software necessary for you to run the SSME (run incus list and seess-mgmt). To create this VM, install.sh installs incus which provides an API for spawning new VMs and the like. Sovereign Stack scripts do nearly everything within isolated VMs, minimizing the impact Sovereign Stack has on host OS.
Volume Mounts
When the SSME is created, several directories on the bare metal management machine are mounted into the ss-mgmt VM including:
~/sovereign-stackis mounted into the SSME at/home/ubuntu/sovereign-stackso the SSME has access to the Sovereign Stack Scripts.~/.sshis mounted into thess-mgmtvm at/home/ubuntu/.ssh. All remote VMs are pre-loaded with the~/.ssh/id_rsa.pubssh pubkey so your SSME and bare metal management machine can SSH into VMs in remote Deployments.- Most important of all,
~/ssis mounted into the VM at/home/ubuntu/ss. This path stores all yourremote.conf,project.conf, andsite.conffiles, as well as any generated artifacts and encrypted duplicity backups of the user data (i.e., websites) in your deployments. - If
~/.bitcoinexists, the SSME gains access to bitcoin/test block and chainstate data. This allows the SSME to upload that data to zfs storage volumes residing on remote cluster hosts. This means deployments can start block download from a pre-validated and known position, reducing the time it takes for each full node to reach the respective chain tip. (Note: this under development.)